Event Payload Format
When an event occurs, we send a POST request with a payload in this structure:Supported Event Types
We notify you for these events:| Event Type | Description | Details |
|---|---|---|
prompt_template_version_created | When a new version of a prompt template is created. |
|
prompt_template_name_changed | When a prompt template’s name is changed. |
|
prompt_template_deleted | When a prompt template is deleted. |
|
prompt_template_label_created | When a new release label for a prompt template is created. |
|
prompt_template_label_deleted | When a release label for a prompt template is deleted. |
|
prompt_template_label_moved | When a release label is moved between prompt template versions. |
|
prompt_template_label_change_requested | When a change to a protected release label is requested and requires approval. |
|
prompt_template_label_change_approved | When a pending change to a protected release label is approved. |
|
prompt_template_label_change_denied | When a pending change to a protected release label is denied. |
|
prompt_template_updated | When a snippet imported in a prompt template is updated. |
|
agent_run_finished | When an agent (workflow) run is completed. Note: This event may fire multiple times for the same execution and is not triggered for runs from the dashboard, only when called via SDK or API. |
|
report_finished | When a evaluation report is completed. |
|
dataset_version_created_by_file | When a dataset version is successfully created from a file upload. |
|
dataset_version_created_by_file_failed | When dataset file processing fails. |
|
dataset_version_created_from_filter_params | When a dataset version is created from filter parameters. |
|
Example Payload
Configuring a Webhook
To set up a webhook, go to the Webhook section in the Settings page. Enter the URL of the endpoint you want to send the webhook to and click Submit.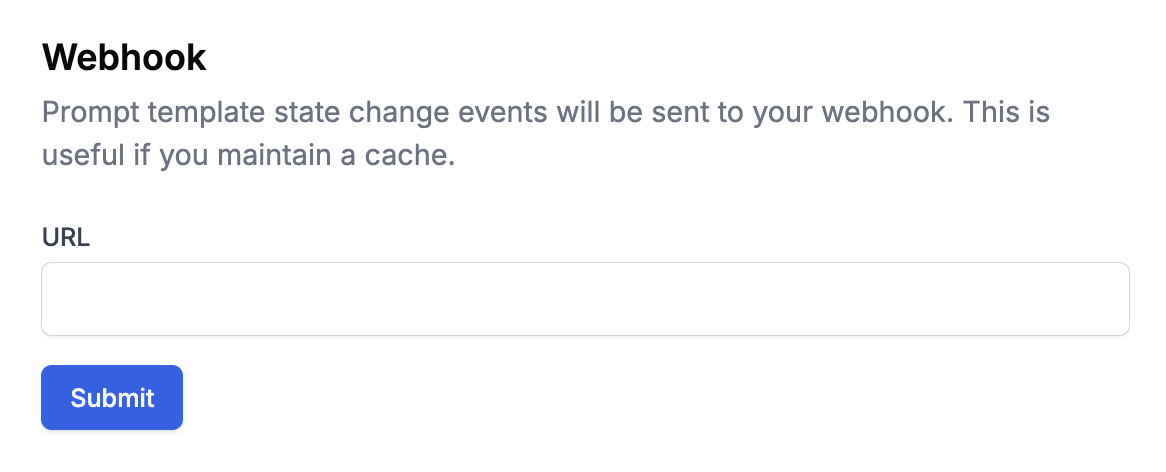
Securing Your Webhook
When you create a webhook, you’ll receive a webhook secret signature that looks like this:
X-PromptLayer-Signature header of each webhook request.

